What is SQL Injection?
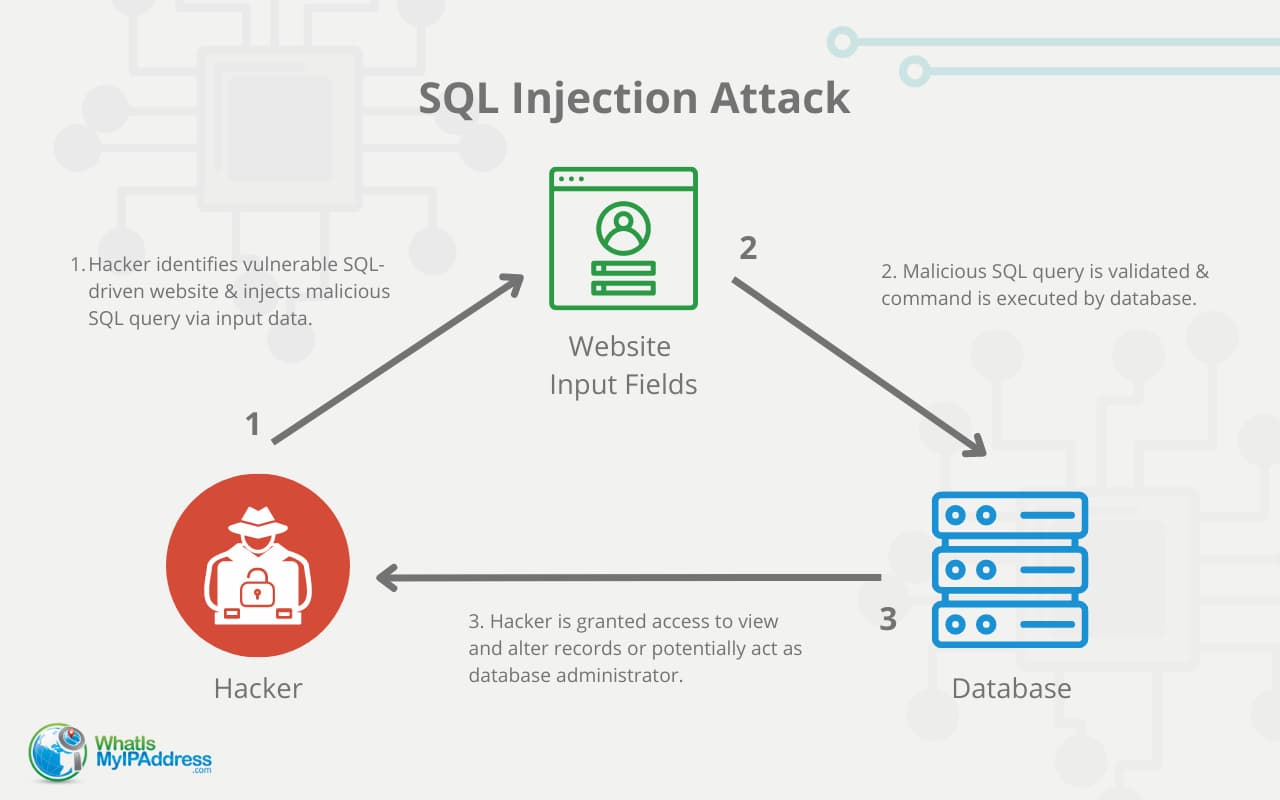
SQL Injection is a type of cyber attack that targets databases through malicious SQL code. It occurs when an attacker exploits vulnerabilities in a website's input fields, such as login forms or search bars, to inject unauthorized SQL commands. These commands can manipulate the database, allowing the attacker to access, modify, or delete sensitive data. SQL Injection is one of the most common and dangerous web application vulnerabilities, often resulting from improper input validation or insecure coding practices.
Capabilities of SQL Injection
If an attacker successfully performs an SQL Injection, they can gain significant control over the database. This includes the ability to extract sensitive information like usernames, passwords, credit card details, or personal data. In more severe cases, attackers can modify or delete database records, disrupt website functionality, or even gain administrative access to the entire system. Additionally, SQL Injection can be used as a stepping stone for further attacks, such as deploying malware or compromising other parts of the network. The consequences can be devastating, leading to data breaches, financial losses, and reputational damage for the affected organization.
Táblázat részletes leírása (kattints a megnyitáshoz)
Common SQL Injection Examples
| Attack String | Description | Example Query |
|---|---|---|
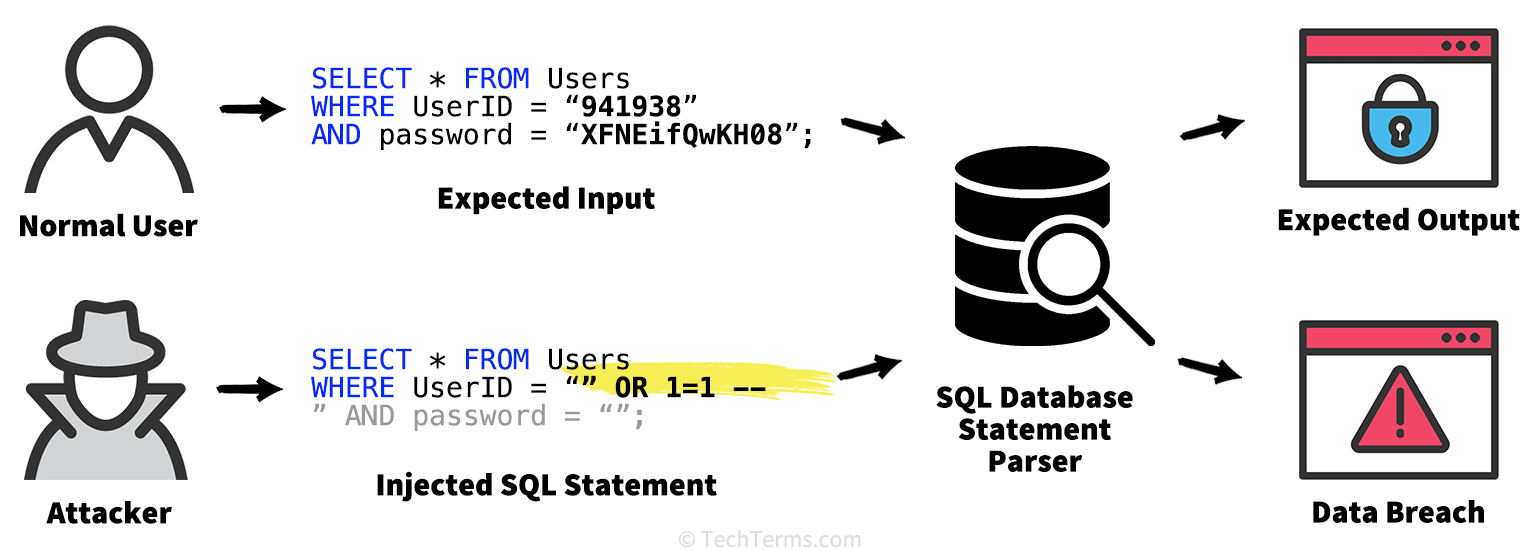
| ' OR '1'='1' -- | The attacker enters ' OR '1'='1' -- into a login form. This modifies the SQL query to always return TRUE, bypassing authentication | SELECT * FROM users WHERE username = '' OR '1'='1' --' AND password = ''; |
| ' UNION SELECT username, password FROM users -- | The UNION statement allows an attacker to append another query to extract data from another table (e.g., users). | SELECT id, name FROM products WHERE id = '' UNION SELECT username, password FROM users --'; |
| ' ORDER BY 5 -- | The attacker inputs ' ORDER BY 5 -- to find the number of columns in a table. If column 5 does not exist, the database returns an error, revealing information about the structure | SELECT id, name FROM products WHERE id = '' ORDER BY 5 --'; |
| ' AND 1=1 – ' AND 1=1 -- | Used when the database does not return errors or visible results. The attacker tests conditions (1=1 returns true, 1=0 returns false). By observing page behavior (e.g., different response times), the attacker can infer information. | SELECT * FROM users WHERE username = 'admin' AND password = '' AND 1=1 --'; |